Readme file
Veeam Kasten installation on IKS
Veeam Kasten is a Kubernetes-native backup and disaster recovery solution designed to protect, move, and manage containerized applications. On IBM Cloud, Kasten provides robust capabilities to ensure the safety and recoverability of your Kubernetes workloads.
IKS (IBM Cloud Kubernetes Service) is a managed Kubernetes service to create your own cluster of compute hosts where you can deploy and manage containerized apps on IBM Cloud.

Security and Compliance Controls
- RBAC
- Data Encryption AES-256-GCM
- Auth Integrations
- Audit/Logging
- SIEM Integrations
- 2 week releases/security updates
- Secure by Design
The aim of this ReadMe is to guide you through a full deployment of Kasten on a cluster IKS.
Estimated duration: 90 mins including the infrastructure provisioning
Before you begin
This ReadMe requires the following command lines:
This ReadMe has been tested with the version IKS v1.29 and Veeam Kasten v7.0.5.
Required resources
To run the software, the following resources are required:
- IKS Cluster
- Persistent Storage that supports VolumeSnapshot capabilities
- Access from the cluster to the Kasten image repository at https://charts.kasten.io/
Provision a cluster IKS via Terraform
These Terraform scripts will provision the following Cloud Services:
- 1 Resource Group
- 1 VPC
- 3 Subnets spread out across 3 Zones
- IKS cluster version 1.29 with 2 nodes of each 4x16 (https://cloud.ibm.com/kubernetes/catalog/create)
- 1 Key Protect service to encrypt resources.
Follow those steps:
-
Clone this repository
-
Login to IBM Cloud
-
Create and store the value of an API KEY as environment variable
If the variable "ibmcloud_api_key" is set in your provider,
you can initialize it using the following command
export TF_VAR_ibmcloud_api_key="Your IBM Cloud API Key" -
Go to the Terraform directory
-
Terraform must initialize the provider before it can be used.
-
Review the plan
-
Start provisioning.
Estimated duration: 30 mins
Connect to an IKS cluster
-
Replace the cluster-name (including <>) with the the cluster name.
-
Log in to the IKS cluster using the following command:
-
Set the values of both the ingress subdomain and the ingress secret of your cluster. Those values will be used in the deployment yaml later.
-
Verify the values you set
Installing the software
Install K10 Dashboard
-
Add the Kasten Helm charts repository using the following command:
-
Run a repo update to get the latest Kasten version.
Note: you can see the version by running the command:
helm repo list --versions -
Create the namespace where Kasten will be installed. By default, the installation creates the namespace kasten-io.
-
Install Kasten K10 in IKS using the following Helm command:
Use this command to install on OpenShift
helm install k10 kasten/k10 --namespace=kasten-io --set scc.create=true -
Check that installation is complete and all pods are up and running in the kasten-io namespace:
Note: It takes 3 mins to get all the pods up and running.
-
Check the status of PVC
-
Create a route for accessing the Kasten dashboard:
-
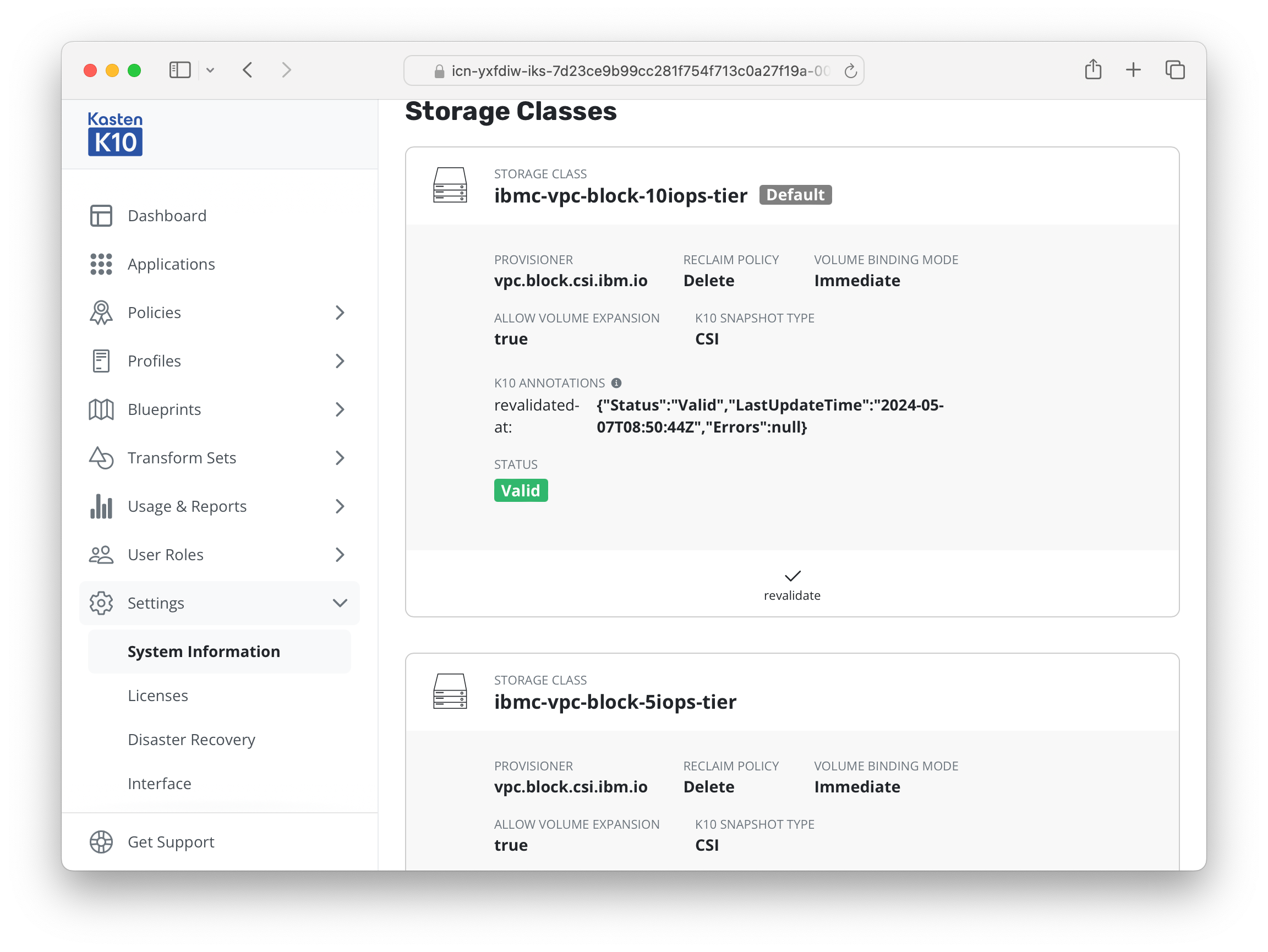
In K10 console, go to the Settings > System Information. Scroll down to Storage Classes.
-
Click on Validate button on the right hand side in the storage class ibmc-vpc-block-10iops-tier
-
After the few seconds, the status should become Valid.
Create Location profile for IBM COS Smart bucket
Location profiles are used to create backups from snapshots, move applications and their data across clusters and potentially across different clouds, and to subsequently import these backups or exports into another cluster.
Exporting or importing data requires an object storage location. We will use the IBM COS Bucket created via Terraform. IBM COS is an S3-compatible object storage system hosted on IBM Cloud.
-
The COS credentials have been automatically generated by Terraform. You should see the following when your terraform apply completes.
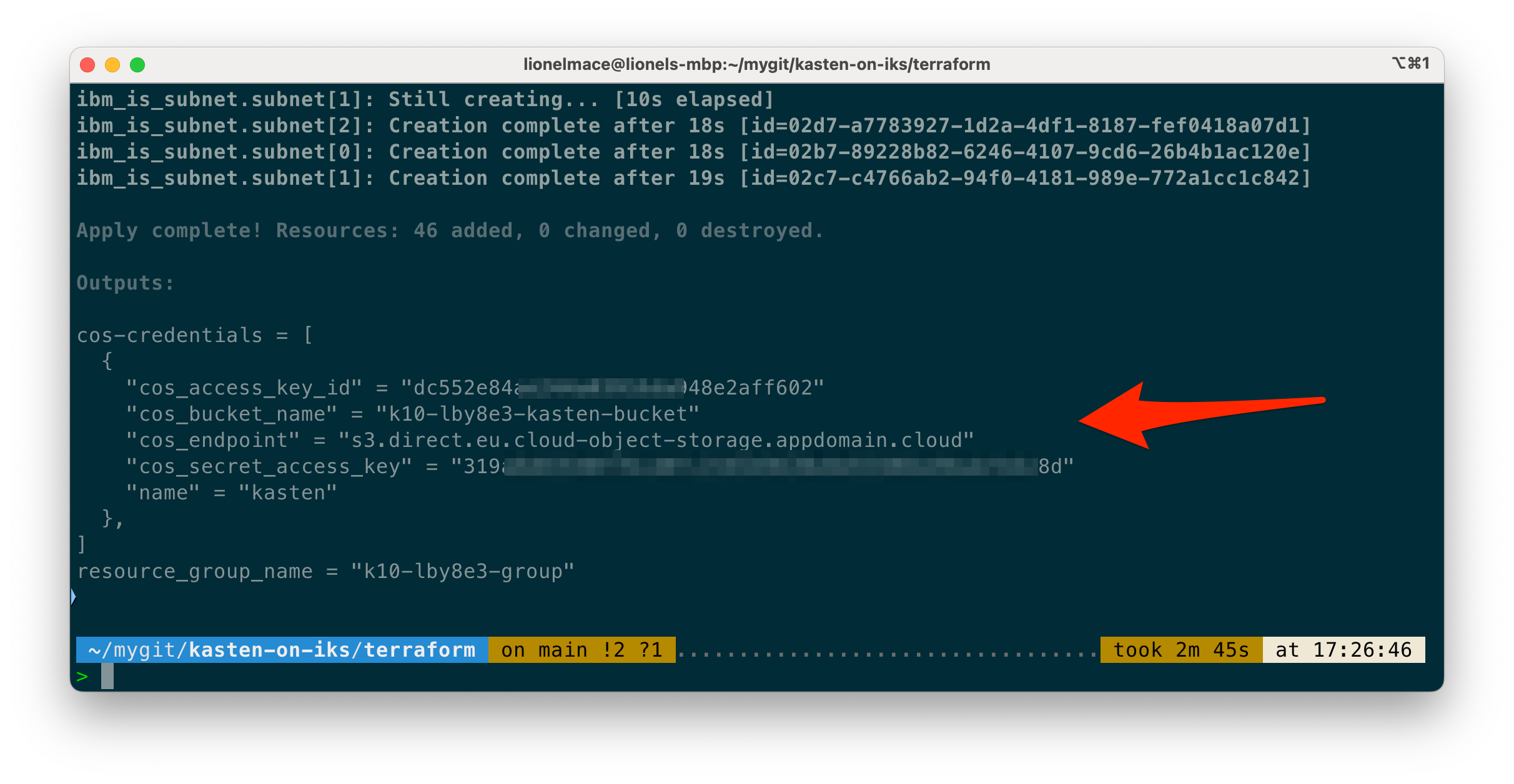
-
Let's set those IBM COS values into variables to reuse them later.
-
Create a Kubernetes secret to store the COS credentials for K10
-
Create Location profile for IBM COS Smart bucket
Uninstalling the software
Uninstalling Kasten can be accomplished via helm commands:
```sh
helm uninstall k10 -n kasten-io
```
Resources
- Kasten K10 Overview
- Kasten Release Notes
- Kasten Supported Kubernetes Version